Critical Users
Manage potential risks and threats caused by vulnerable users
Note: You can view the critical user information for a particular app, like risk level or threat associated with a user, by simply clicking on the Users tab under the individual Applications menu.
The critical users' list can be found right next to the critical apps list under the security module in the Zluri Dashboard. Similar to the table of critical apps, the critical users' tab contains the data table of Critical Users within an organization who currently pose a certain level of risk/threat to the organization by harnessing one or many critical apps which pose a risk to the organization.
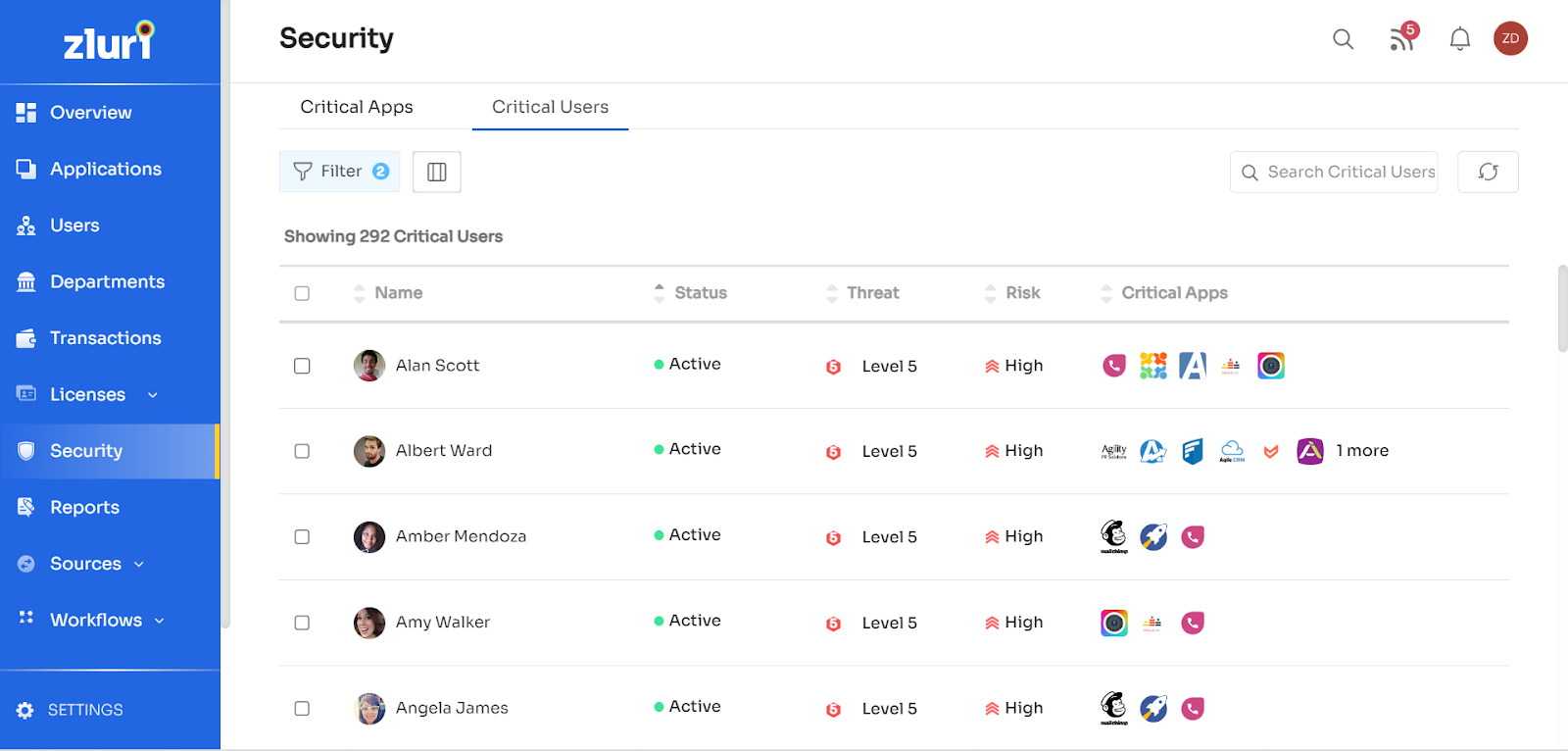
The data table consists of 5 columns:
- Name: Used to identify the name of the critical user.
- Status: This shows whether the critical user is currently active or not.
- Threat: This denotes the current threat score of the user.
- Risk: This is used to denote the current risk level score of the particular critical user.
- Critical Apps: This shows the current critical apps which the given persons are using
Applying filters: On the top of the Critical users' list, you will see a button labelled Filter followed by a number that denotes the number of lists applied to the list.
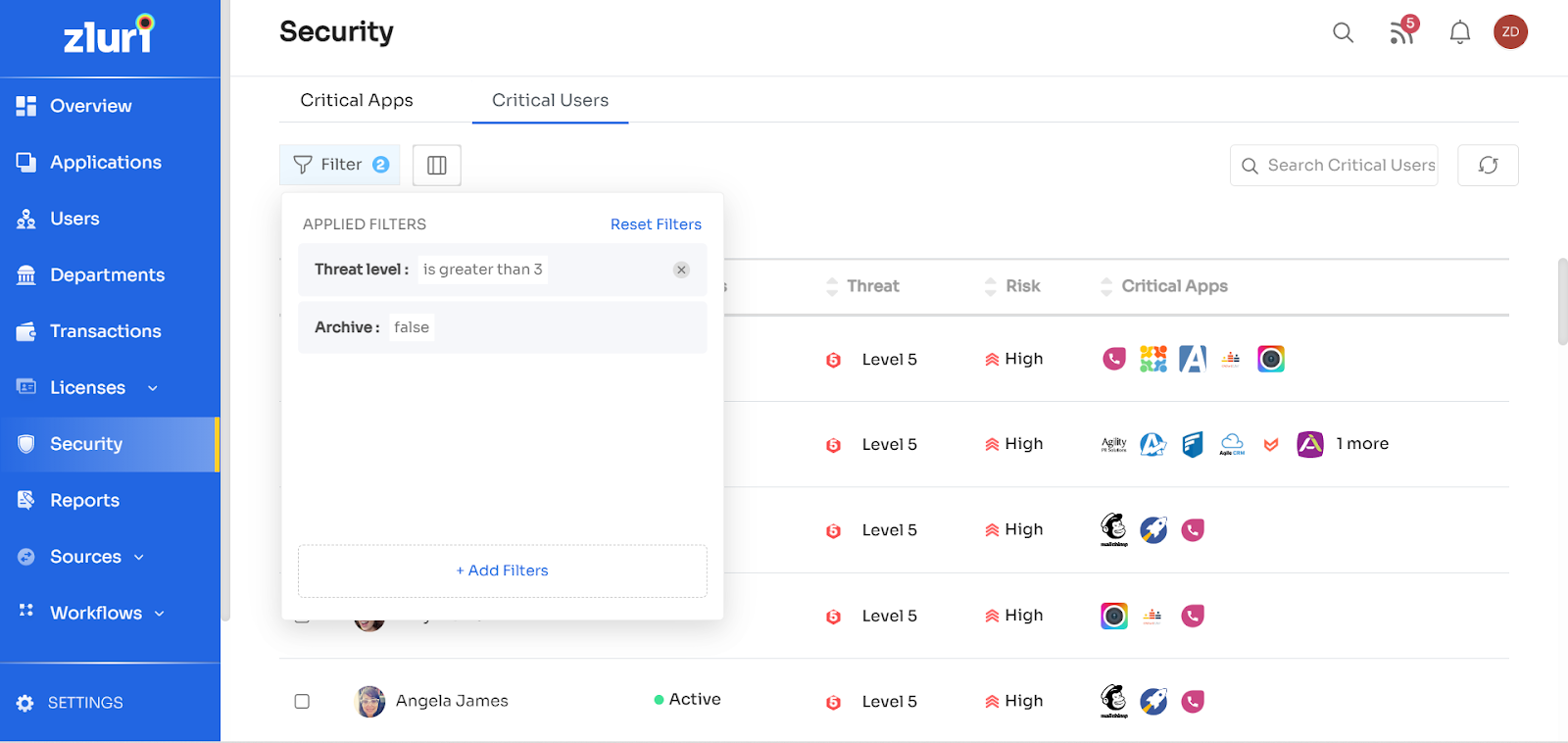
You can add new filters by clicking on the Filter button, and then from the window that opens, click on Add Filters button.
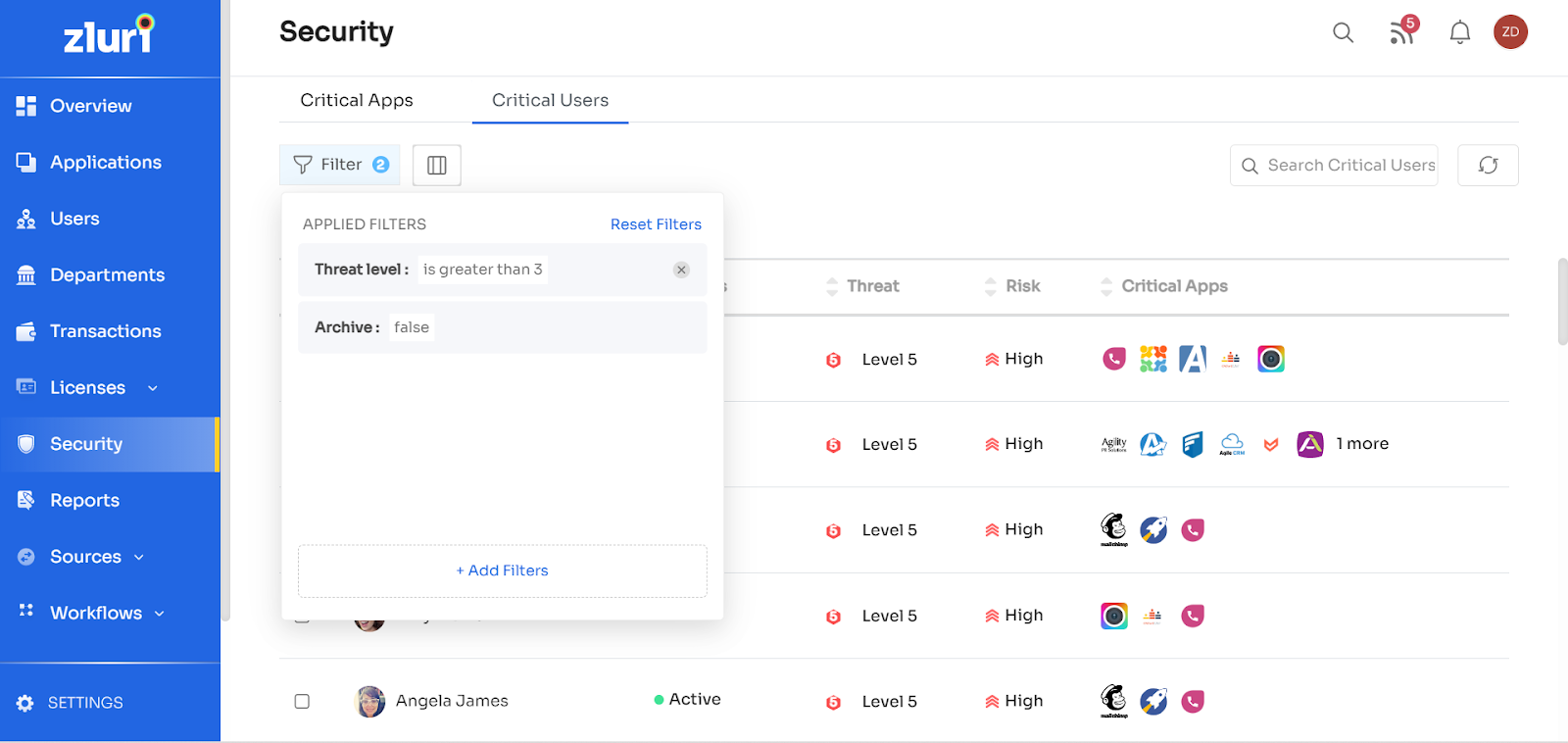
The following set of filters can be applied to the list of critical users:
The filters can be selected based on Archive, status (whether active or inactive), Application Name, Application Id, Threat level (is more significant than), Critical user count, critical scope count (number of scopes that are under risk associated with the app), risk score and risk level.
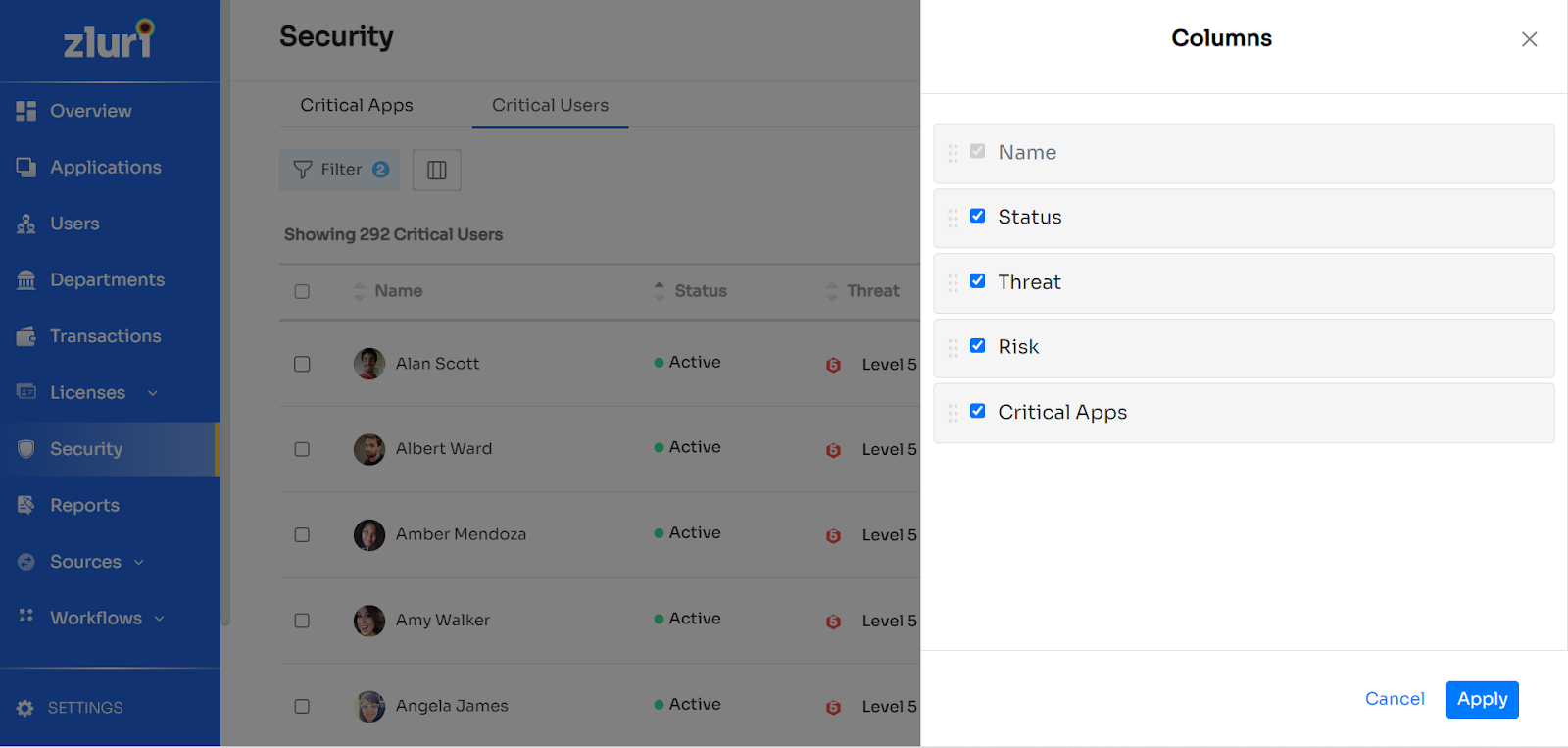
- Applying Columns: You can customise the list by selecting the columns based on which the security information of an app is to be displayed. Just click on the button next to the Filter button to open the Columns menu.
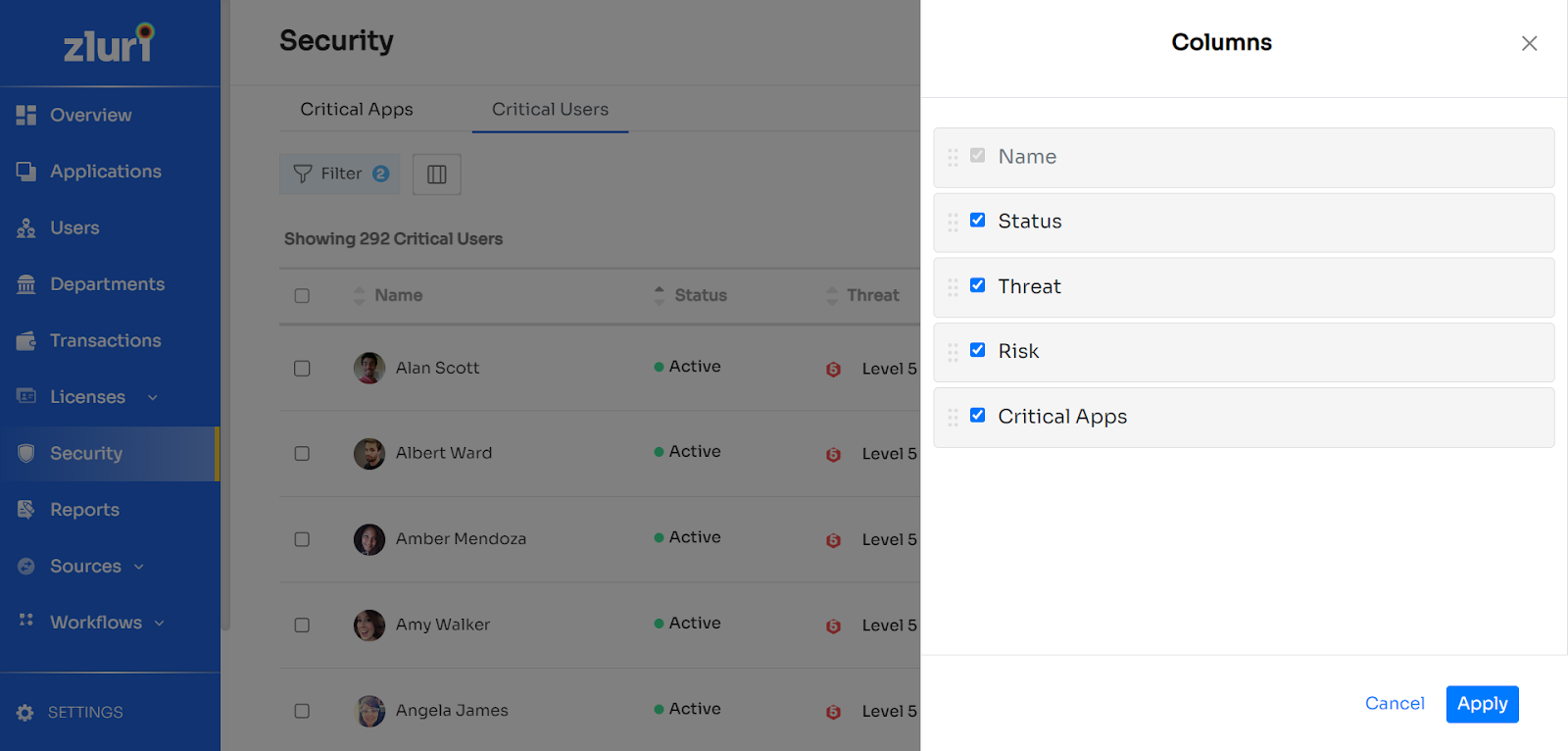
From the above, select the columns you wish to keep and click on apply.
Updated 4 months ago
